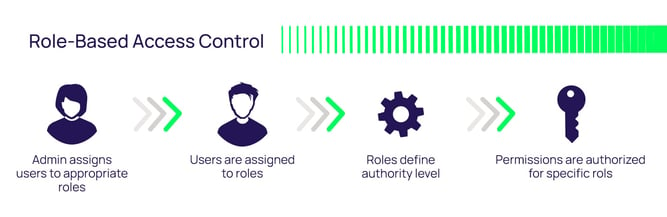
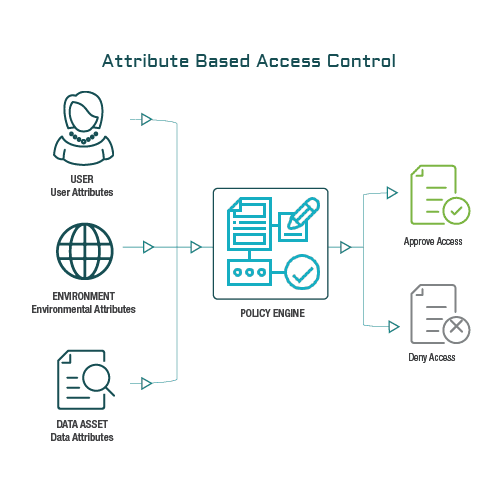
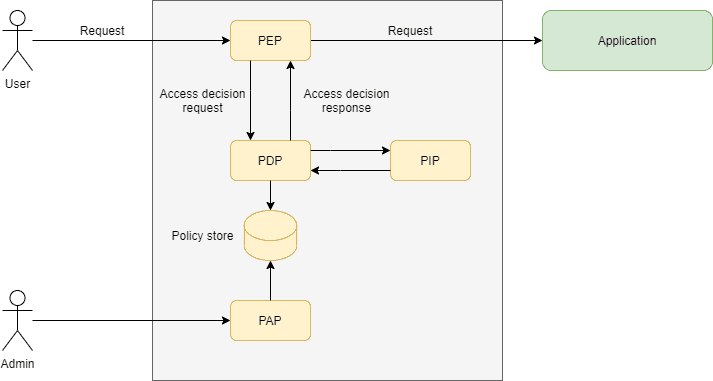
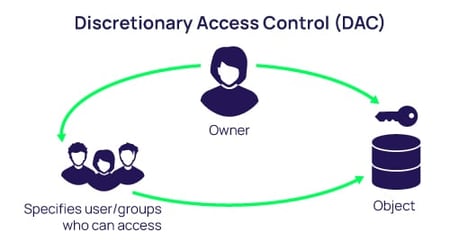
Sensors | Free Full-Text | A Survey of Context-Aware Access Control Mechanisms for Cloud and Fog Networks: Taxonomy and Open Research Issues
![PDF] Analysis of Common Access Control Models and Their Limitations in Cloud Computing Environment | Semantic Scholar PDF] Analysis of Common Access Control Models and Their Limitations in Cloud Computing Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/274d2313b4c103a022a5a974716a00a6dc2d3000/3-Table1-1.png)
PDF] Analysis of Common Access Control Models and Their Limitations in Cloud Computing Environment | Semantic Scholar

![The 4 Types of Access Control Models Explained [+Examples] The 4 Types of Access Control Models Explained [+Examples]](https://butterflymx.com/wp-content/uploads/2023/01/Access_control_models_social.jpg)

![PDF] Review the Types of Access Control Models for Cloud Computing Environment | Semantic Scholar PDF] Review the Types of Access Control Models for Cloud Computing Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4dd58d7ef7f99a18255704c0733da18c49154787/4-Table1-1.png)



![PDF] Review the Types of Access Control Models for Cloud Computing Environment | Semantic Scholar PDF] Review the Types of Access Control Models for Cloud Computing Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4dd58d7ef7f99a18255704c0733da18c49154787/4-Table2-1.png)