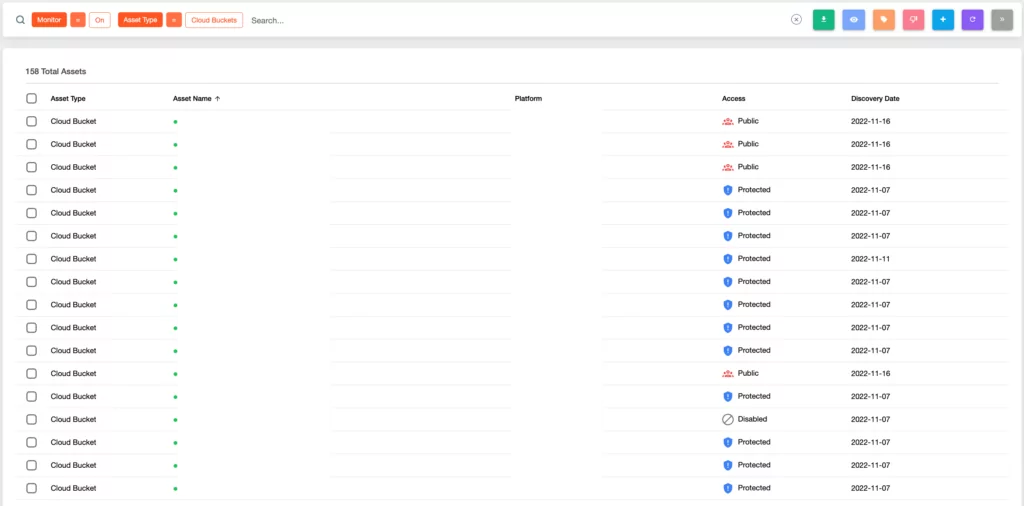
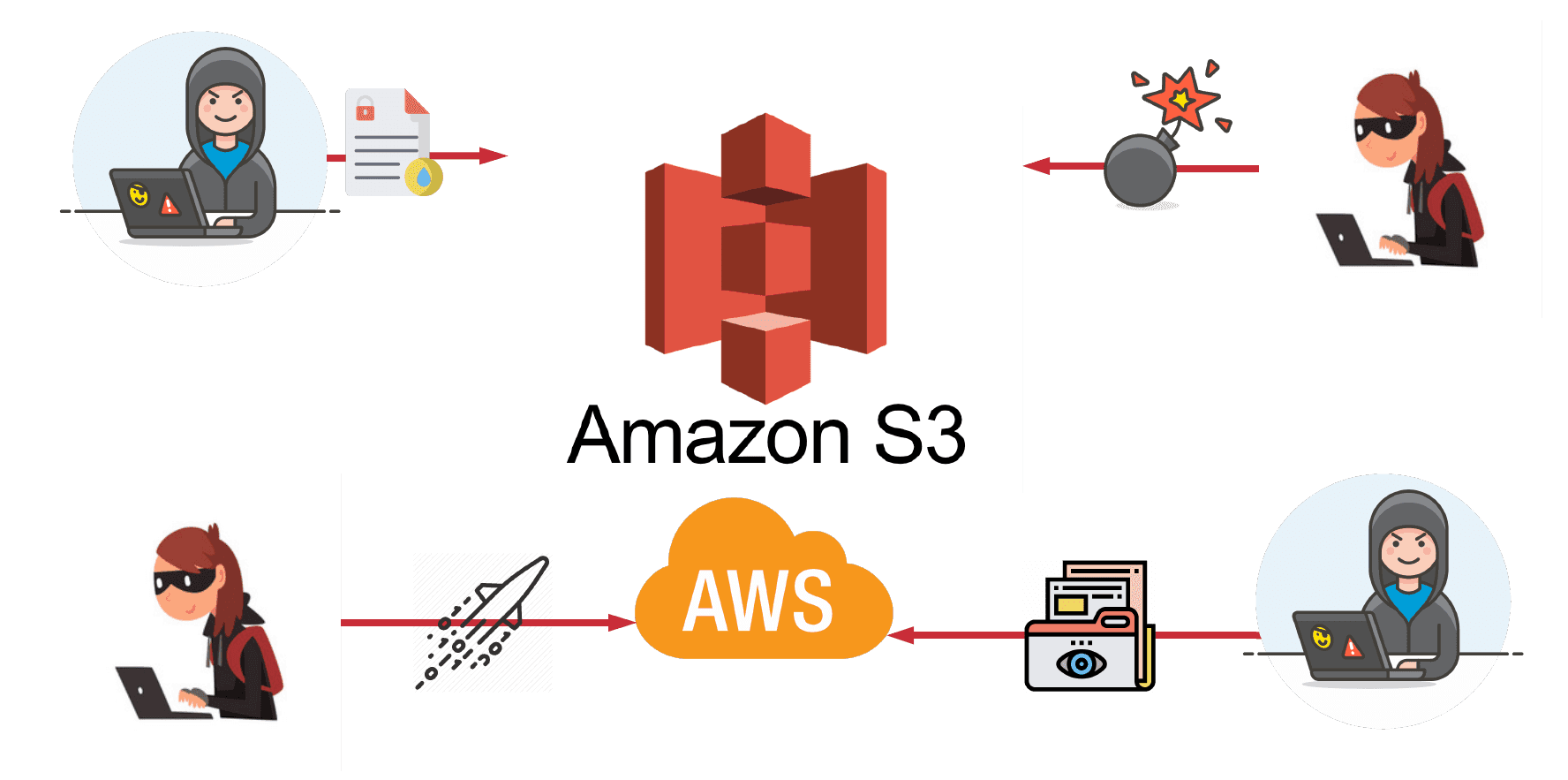
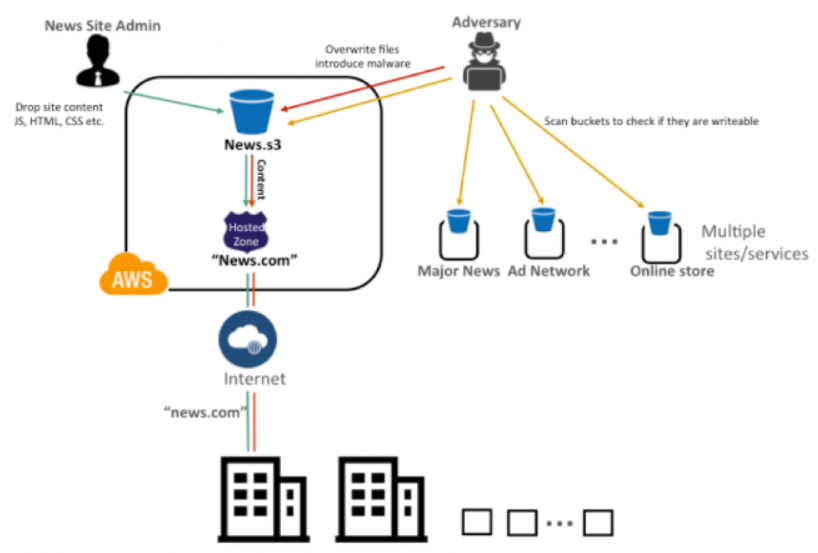
AWS S3 Bucket Takeover Vulnerability: Risks, Consequences, and Detection - SOCRadar® Cyber Intelligence Inc.

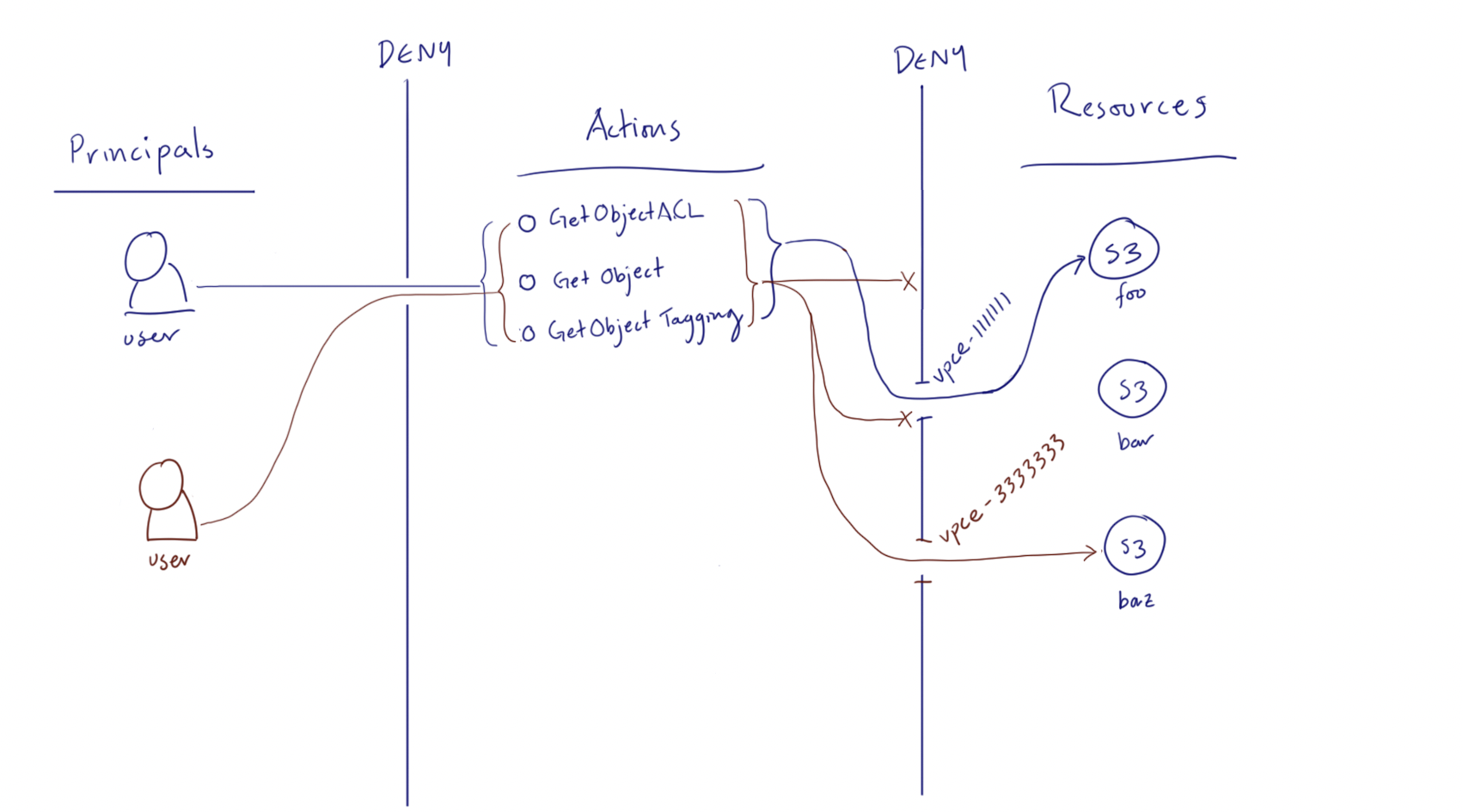
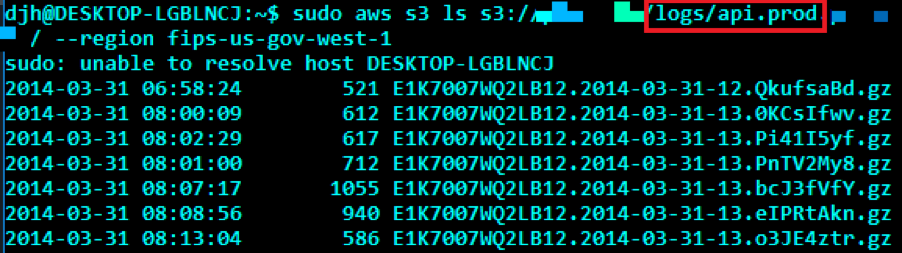
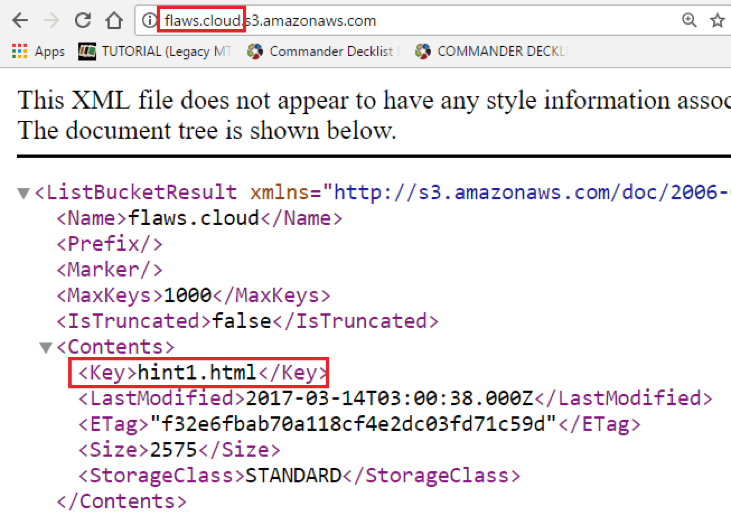
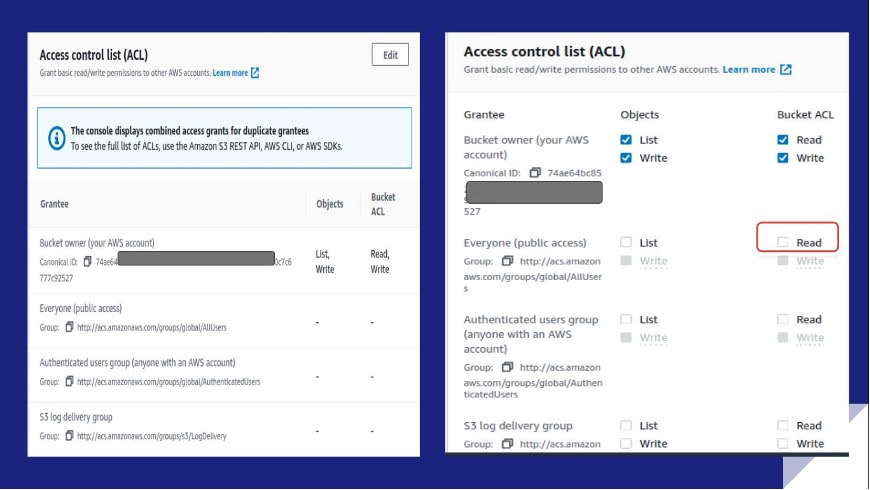
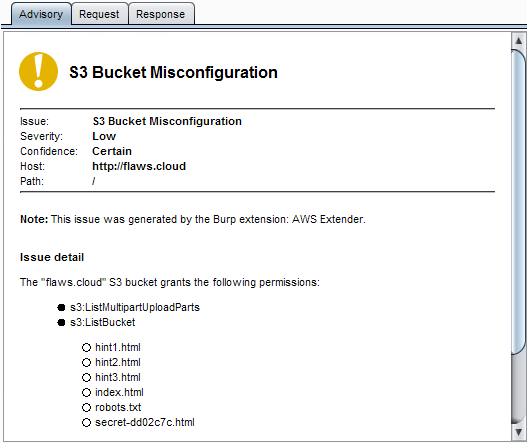
Misconfigured S3 Bucket Access Controls to Critical Vulnerability | by Harsh Bothra | InfoSec Write-ups
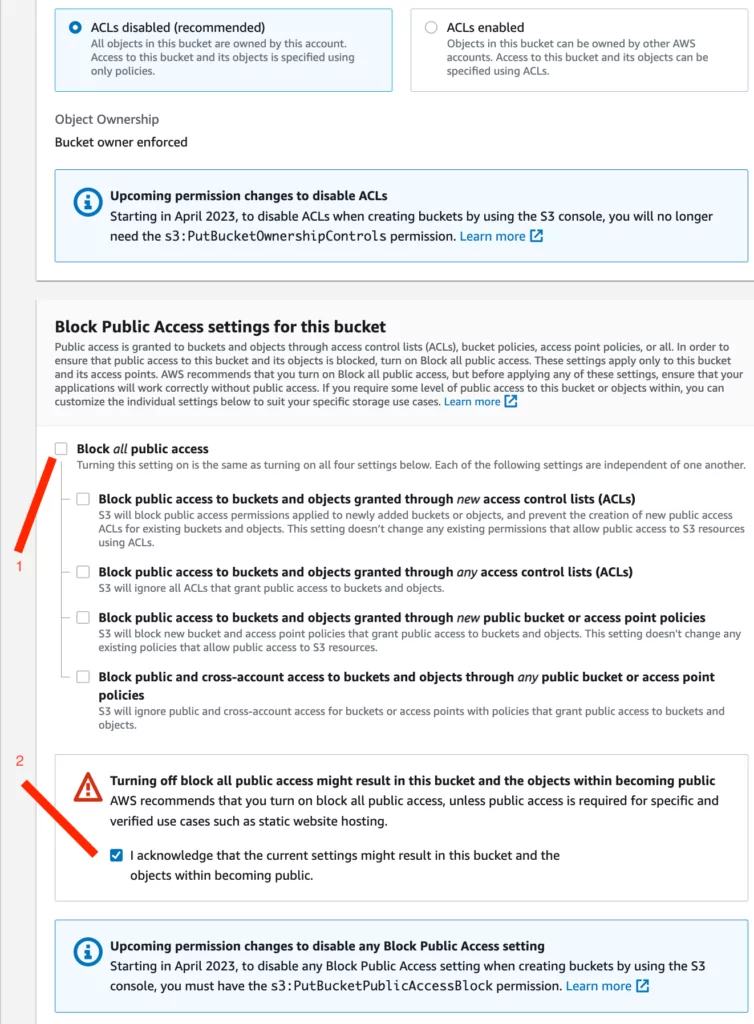
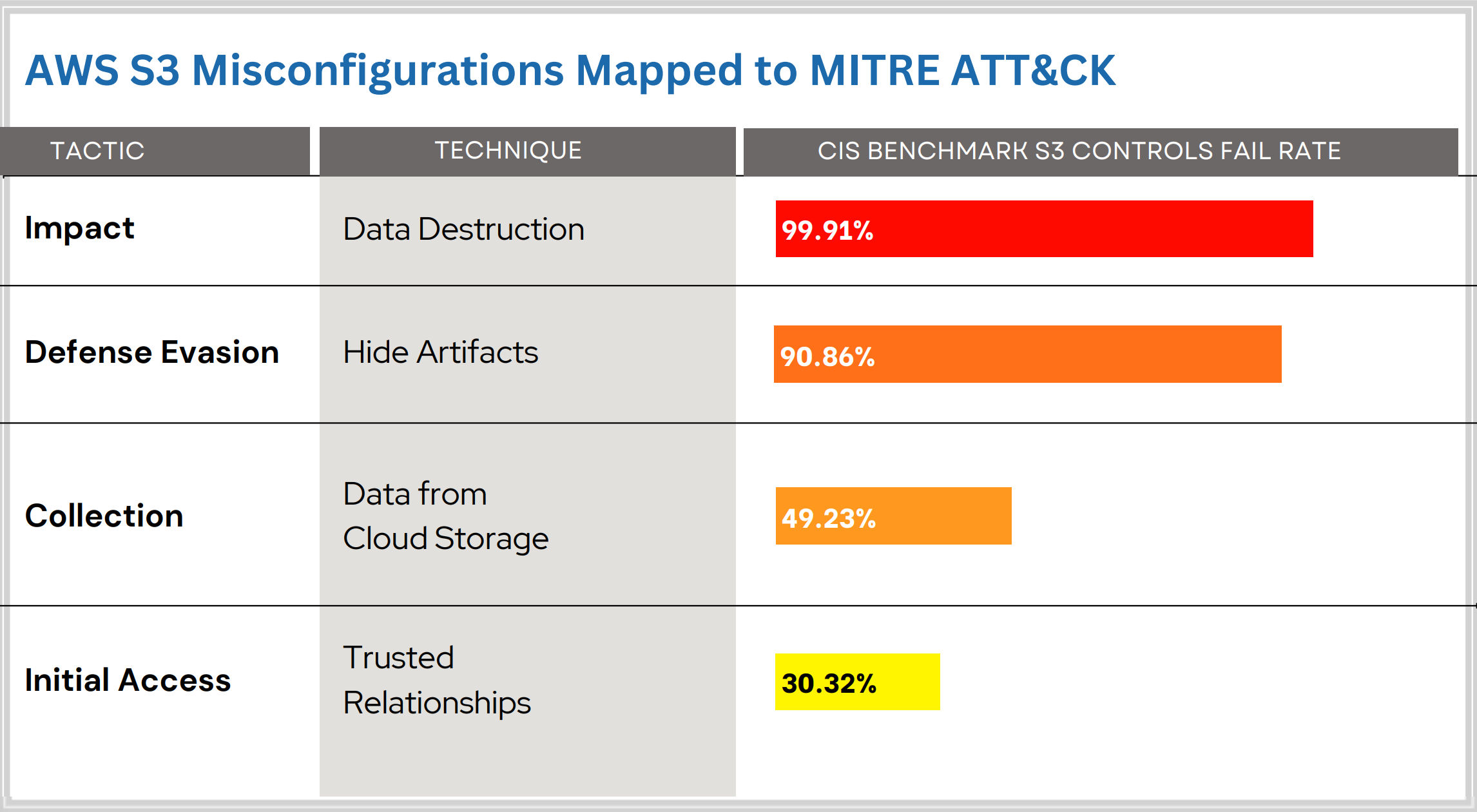
AWS S3 Bucket Takeover Vulnerability: Risks, Consequences, and Detection - SOCRadar® Cyber Intelligence Inc.