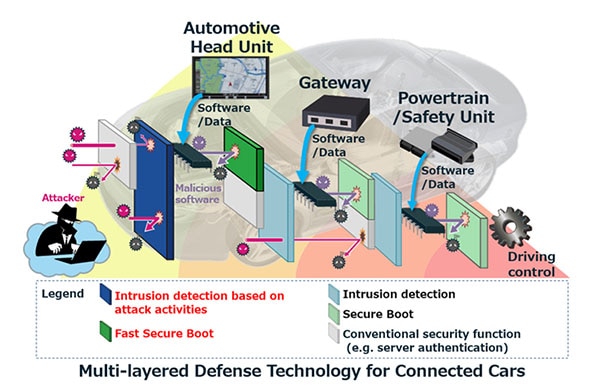
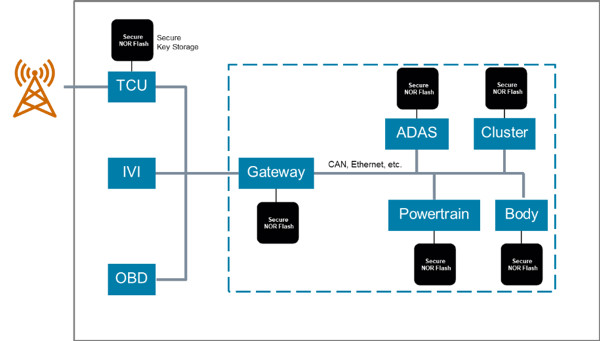
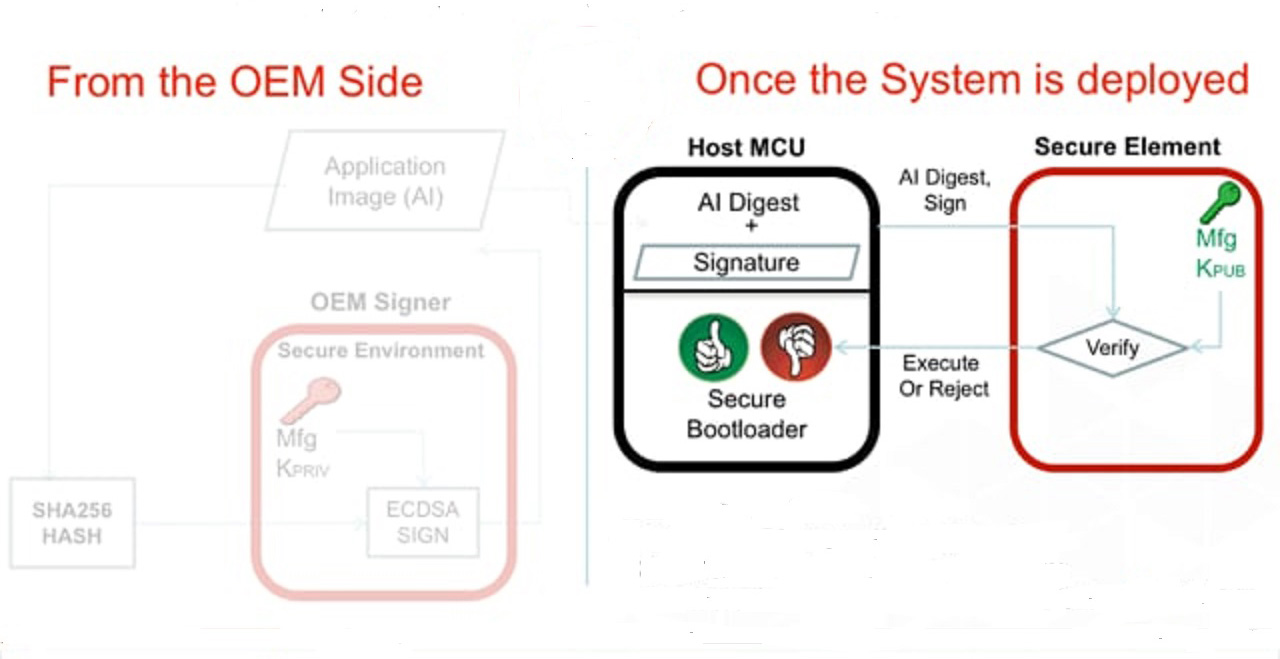
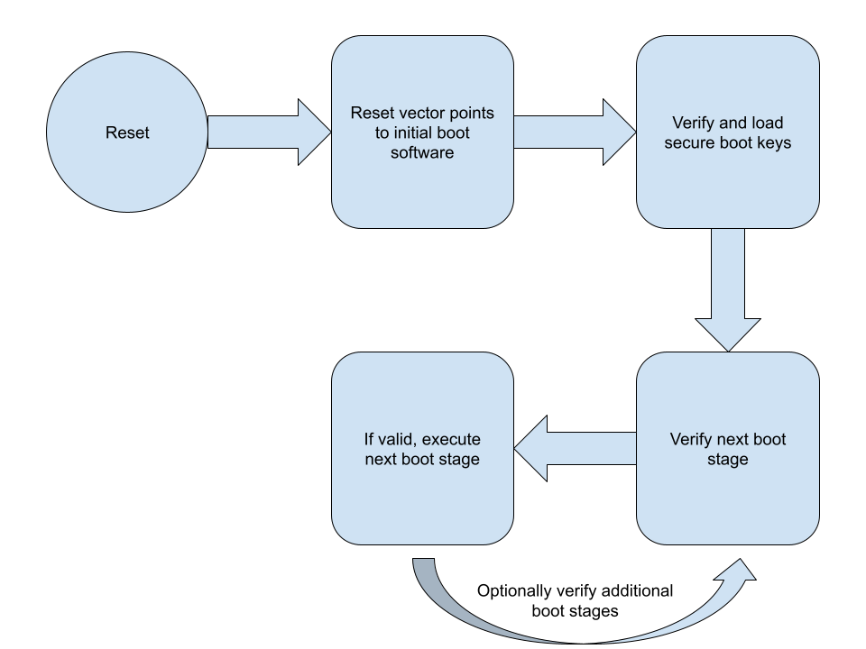
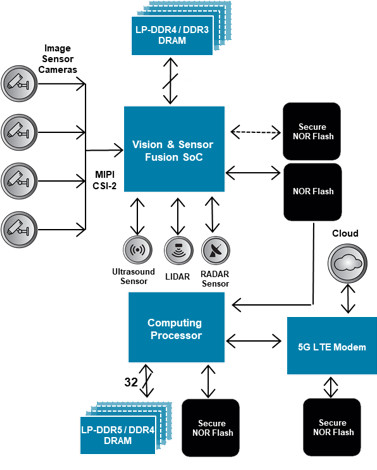
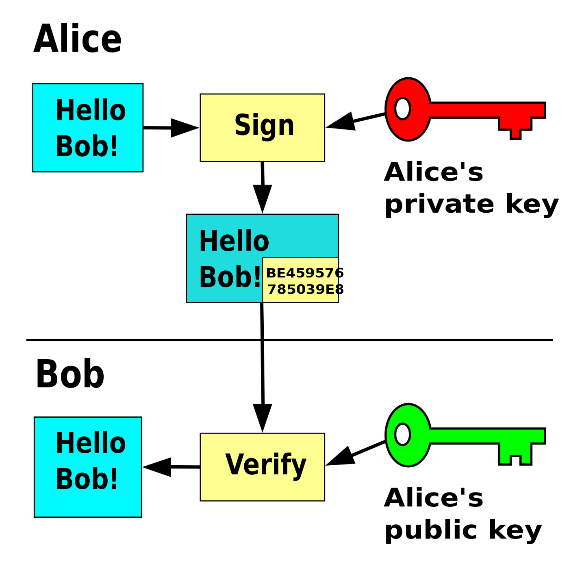
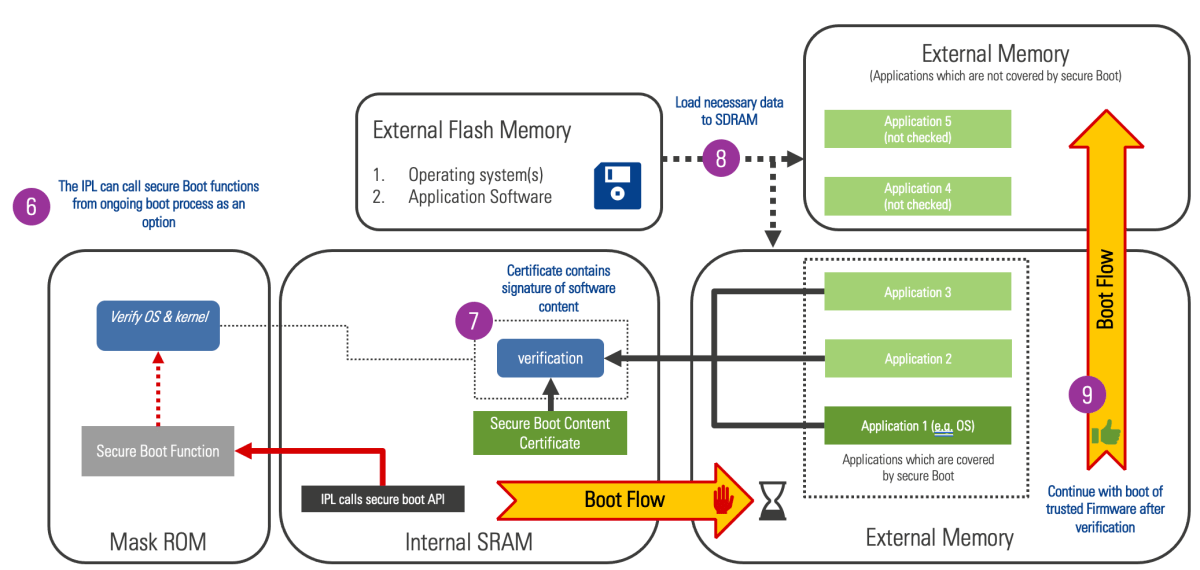
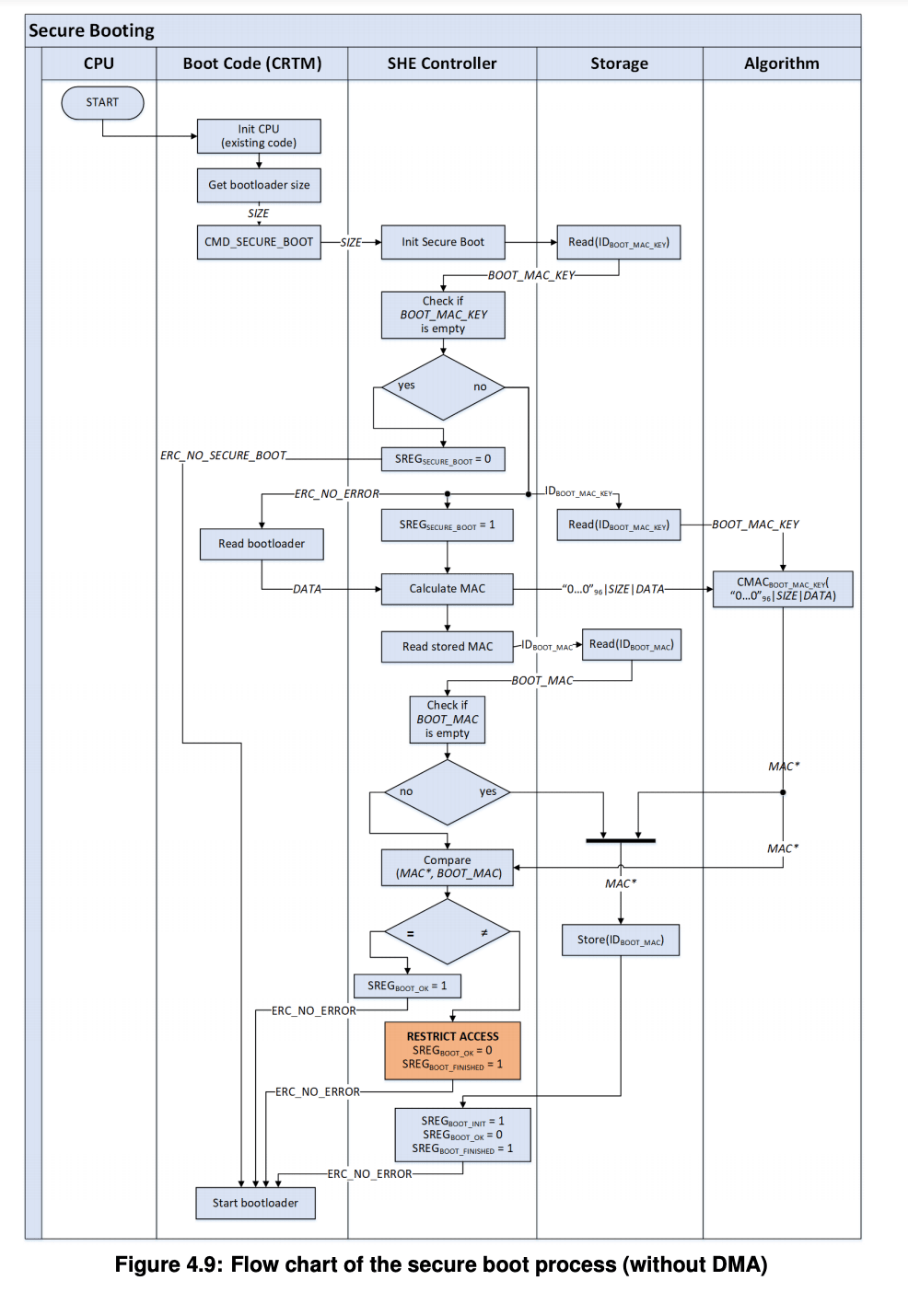
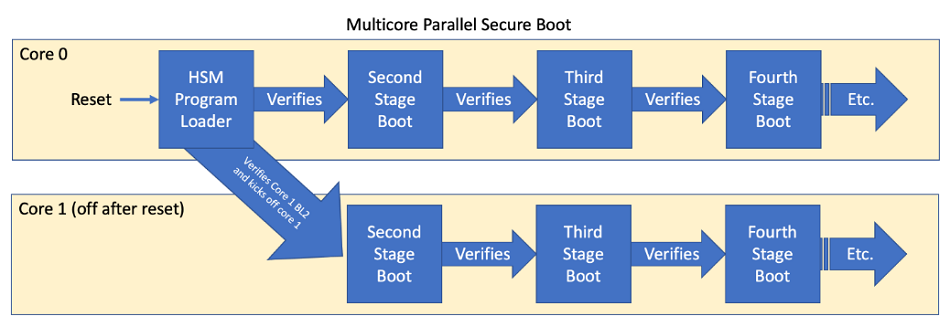
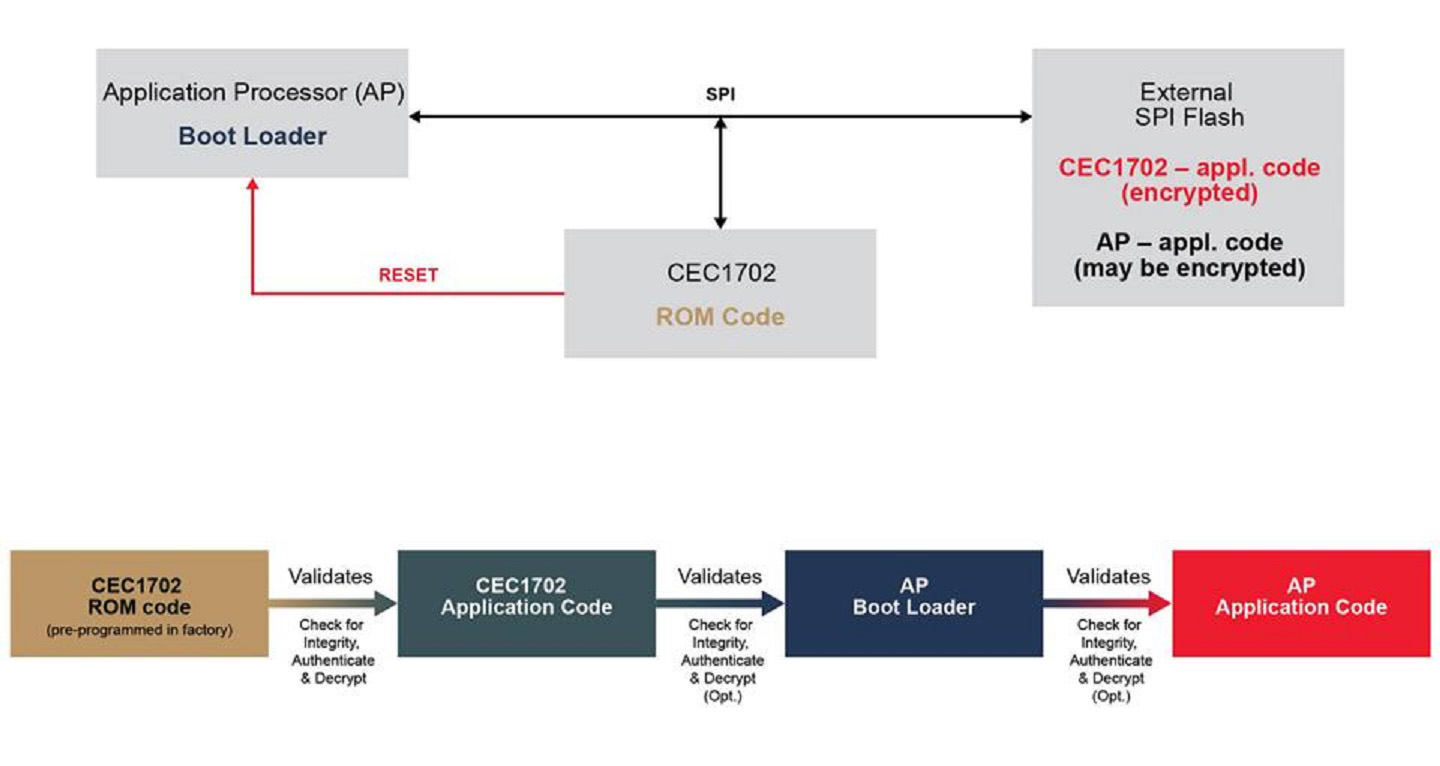
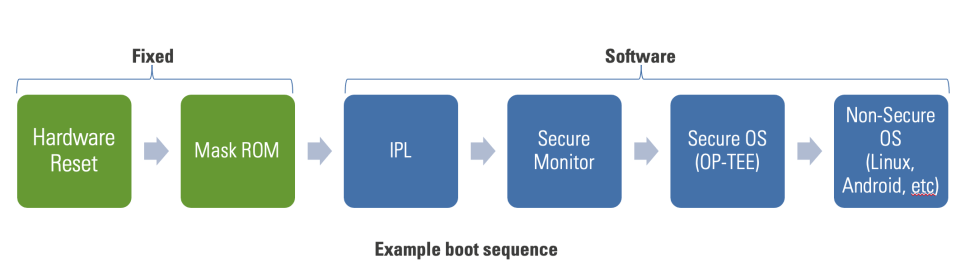
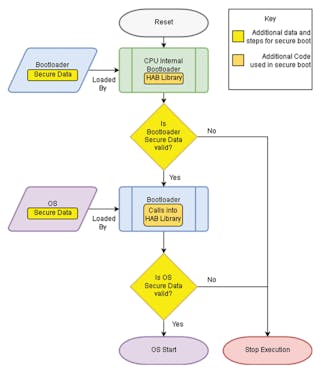
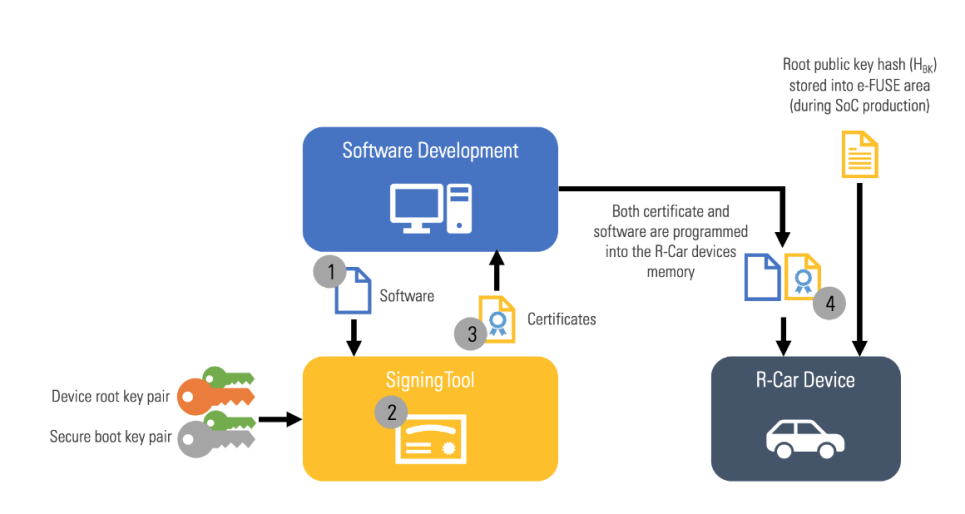
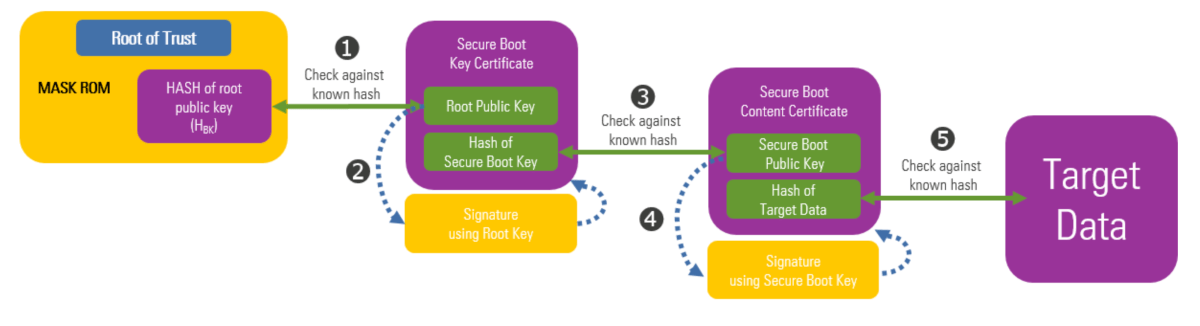
Renesas Electronics - This is the 2nd blog in the #Automotive #Security series which deals with the 2 types of security IP found in our 32-bit RH850 automotive MCU - ICU-S &

Now as a podcast! Secure boot, Automotive Ethernet, standards and regulations - News & Insights - ETAS